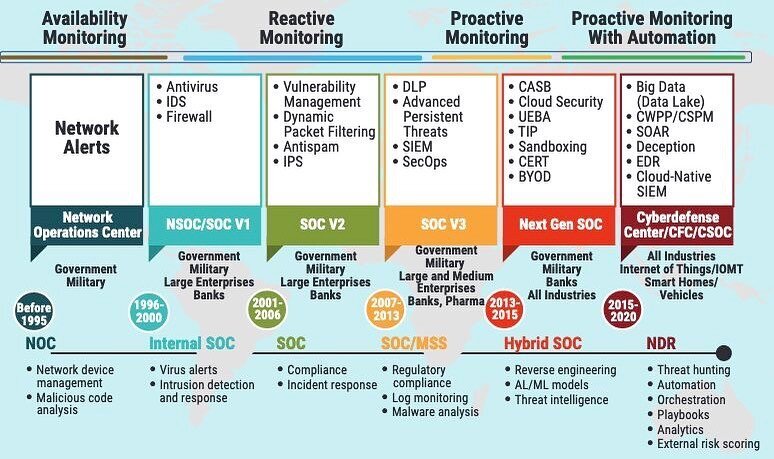
Reaching an all-time high, the cost of a data breach averaged $4.35 mil in 2022.
In today’s security climate, data has become the new currency. Regardless of size, every business has data that’s important to them, which makes them a target. Cybercrime costs include damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, and reputational harm.
FSI recognizes this ever-growing threat landscape and the need to protect our client's digital assets adequately. We deliver cutting-edge cybersecurity solutions to organizations specializing across four pillars: visibility, compliance, threat protection, and data security.
We offer strategy and governance to improve organizational readiness by defining, managing, and measuring cyber risk thresholds. Our advanced cyber defense reduces vulnerabilities, identifies threats, and enhances cyber defenses for faster detection and reduced response time.
Areas of Practice
Virtual Chief Information Officers
One of the most popular small and medium-sized business IT trends today is utilizing Virtual Chief Information Officers (vCISO). We help develop and implement a cybersecurity strategy and roadmap tailored to your organization to improve your security posture and upgrade your defenses.
CYBERSECURITY strategy & ARCHITECTURE
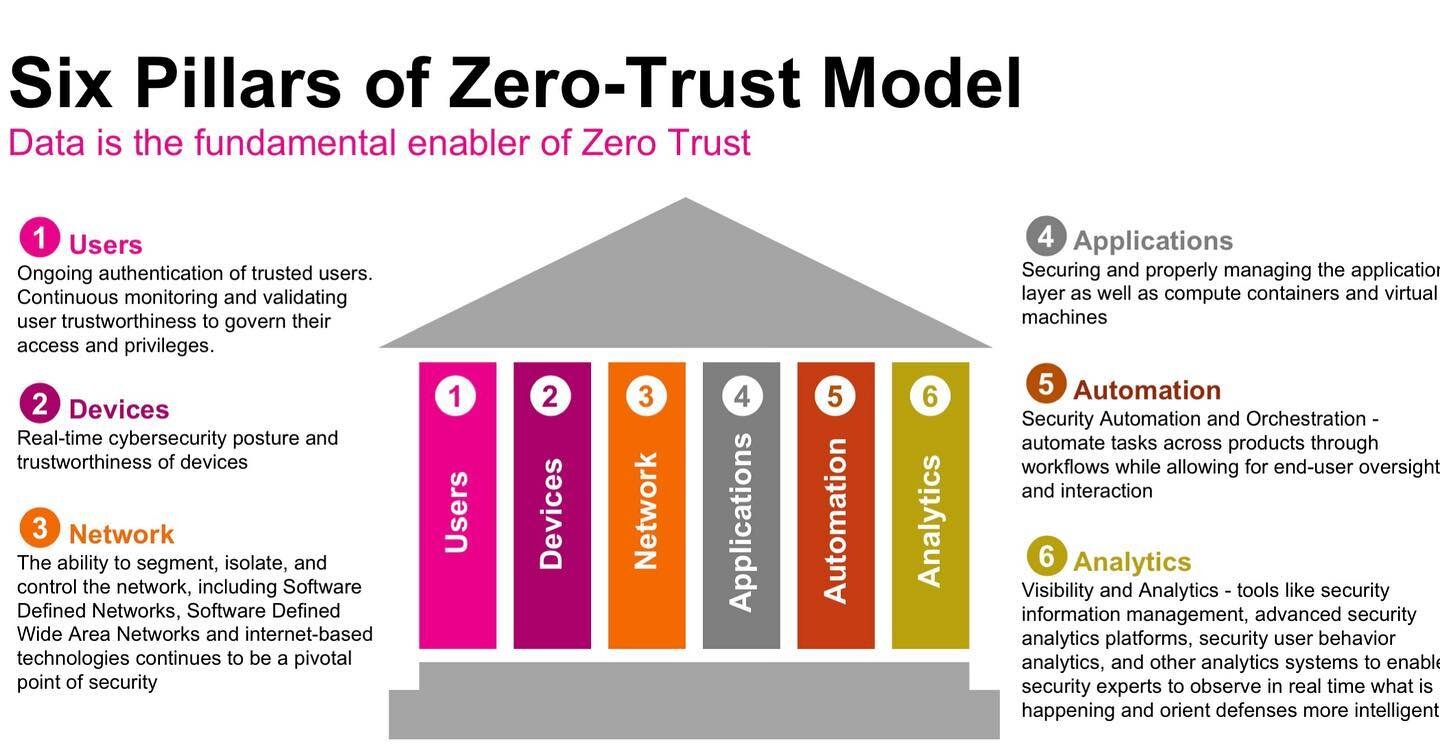
Your organization’s security architecture determines how you install security controls. Without a mature security architecture, your environment may be open to an unknown or underestimated risk level. Our experts understand networking technologies and how they are used to deliver business value.
Cybersecurity Proposal Writing
We can help you develop a technical response to cybersecurity Rfx (RFS, RFI, and RFQs) responses. We have developed a proprietary methodology for developing technical responses to cybersecurity proposals by leveraging our work experience and technical knowledge.
SOC-as-a-Service (SOCaaS)
Our framework addresses all areas of your infrastructure and integrates assessments, governance, compliance, and architecture as a risk management program. This perspective allows us to design a flexible infrastructure to meet your ever-changing needs and maintain a secure/stable environment.
Cybersecurity Career development
Cybersecurity professionals work in every size company and industry to protect organizations from data breaches and attacks. The demand for cybersecurity professionals is growing at a breakneck speed. We can help you develop a tailored plan to start or enhance your cybersecurity career.
Cloud Security
If your organization hosts applications in AWS, GCP, or Azure, security is a shared responsibility between you and your cloud providers. We help you maintain a strong security posture and continuous compliance by automating best practices for your cloud infrastructure environments.
Let's Chat.
Use the form below to contact us regarding your cybersecurity inquiry. Please be as detailed as possible. Include your industry along with any specific document requests. To help us best service your inquiry, we recommend that you first describe the issue you’re having before telling us what you want to achieve. You may also email or call us to make an appointment.